Jonghyun Woo
Editors of ITU-T X.1220
Summary
Among cyber attacks, the two that security teams and operations teams should pay the most attention to are software vulnerability attacks and malware attacks. In this article we examine how large a portion these two attack types occupy in overall cyber attacks and introduce a new international standardized technology that can defend against both simultaneously. Through this we propose a method to build an additional defense layer beyond existing network and endpoint protection systems to prepare for unknown cyber attacks (such as zero-day attacks). In other words, we present measures to keep critical data safe even if attacks abusing undiscovered vulnerabilities or malware in forms that evade detection occur.
Types of Cyber Attacks and Defense Systems by Type
Recently, a variety of cyber attacks targeting telecommunications companies, medical institutions, and government agencies have been occurring one after another. These cyber attacks can be broadly classified into four categories based on their operational methods.
1. Software vulnerability attacks
2. Malware attacks
3. Phishing attacks
4. DDoS (Distributed Denial of Service) attacks
Among these, software vulnerability attacks exploit flaws in operating systems or business applications we use, allowing the attacker to take over administrator privileges. Through these flaws an attacker secures administrator rights on a PC or server and executes commands as if they were a legitimate user. As a result, they can exfiltrate internal data or encrypt it (ransomware), causing damage. PC or server operators must regularly apply patches and updates to defend against this, but in practice software vendors often cannot provide patches quickly, and there are many cases exploiting zero-day vulnerabilities that have not yet been publicly disclosed.
The second attack type is malware. Malware attacks infect systems with malicious programs and continuously perform malicious actions in the background. Attackers distribute malicious code via email attachments, malicious links, drive-by downloads, etc., and the infected devices can cause various harms such as data leakage, information collection, remote control, and keylogging. Particularly, advanced malware uses evasion techniques such as obfuscation or rootkits to bypass antivirus and security solutions, making detection and removal difficult.
The third is phishing. Phishing is a social-engineering attack technique that impersonates a trusted sender or service to steal personal information or authentication credentials. Attackers deceive users via email, SMS, messengers, or fake login pages to induce entry of passwords, OTPs, card information, or to install malware. Because phishing targets “human trust” rather than a technical vulnerability, it is easy to be careless; targeted (spear-phishing) attacks in particular have higher success rates and larger impacts. Efforts such as applying strong authentication methods, preblocking suspicious links, regular security training, and phishing simulation drills aim to reduce user vulnerabilities, but ultimately it is impossible to completely prevent users from being deceived by attackers.
Finally, DDoS attacks concentrate excessive traffic on a specific server or service using many distributed devices, making normal service provision impossible. Attackers exploit botnets or cloud resources to saturate network bandwidth or consume application resources, reducing service availability.
Large-scale DDoS attacks can cause service outages, financial loss, and reputational damage for businesses. To mitigate this, traffic scrubbing and filtering, edge CDNs, or cloud-based mitigation services can be applied, but it is impossible to preemptively block all excessive traffic that comes in over public networks.
| Category | Main techniques | Main targets | Objective (Outcome) | Defense methods | Proportion |
| Software vulnerabilities | Exploit vulnerability → privilege escalation | Servers · Cloud · Applications | Steal admin privileges → internal access | Patch / Update | 25% |
| Malware (ransomware) | Install / execute malicious code | Personal PCs · Servers · Medical devices | Data encryption · Data exfiltration · Monetary demands | Anti-virus / EDR | 30% |
| Phishing · Social engineering | Deceptive emails / messages | Employees · User accounts | Account takeover → internal intrusion | Phishing-resistant MFA | 40% |
| DDoS | High-volume traffic attacks | Services · Web portals | Service outage · Business interruption | Traffic scrubbing | 5% |
Among the four attack types, rather than focusing primarily on preparing for phishing attacks that deceive employees or DDoS attacks that send traffic over public networks, it is more realistic for security officers and system operators to prepare for software vulnerability attacks and malware attacks. Especially because these two types together account for more than half of all cyber attacks, strengthening defenses in these areas is the most effective way to raise overall security posture.
Limitations of Existing Defense Systems and Establishment of a New Defense Standard
What security officers and system operators currently use as preventive measures are constant updates to minimize software security vulnerabilities and adding network protection and endpoint protection to shield systems. However, these systems can only develop patches or block attacks if they “already know about the vulnerability, malware, or intrusion behavior.” A blacklist approach that blocks known attacks cannot prevent newly appearing vulnerabilities, malware, or intrusion behaviors.
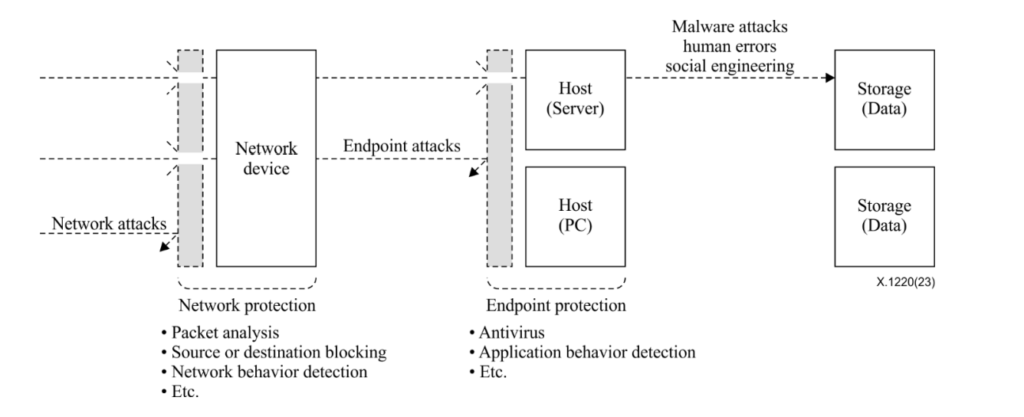
Theoretically, a whitelist approach can be used so that only “registered network packets” or “allowed programs” operate, but it is practically very difficult to run a whitelist on network nodes shared across all systems or on endpoints where many pieces of software run. It is impossible to predict how a system’s network packets might change, and with operating system patches being released daily, re-registering everything each time is inefficient.
Therefore, even if security officers or system administrators consistently apply updates to protected systems, keep antivirus signatures up to date, and monitor network traffic as part of a layered defense, an attacker who exploits a software vulnerability unknown to us, attacks while a patch is being prepared, develops new malware that circumvents existing antivirus inspection, or distributes malware that operates in new behavioral modes to evade behavior-based detection engines may still cause theft or encryption of valuable data.
To solve this problem, the ITU-T, an international standardization body under the UN, established a new storage protection approach as an international standard — ITU-T X.1220 — that applies whitelist access control at the storage layer where data is stored, rather than at shared network or endpoint layers.
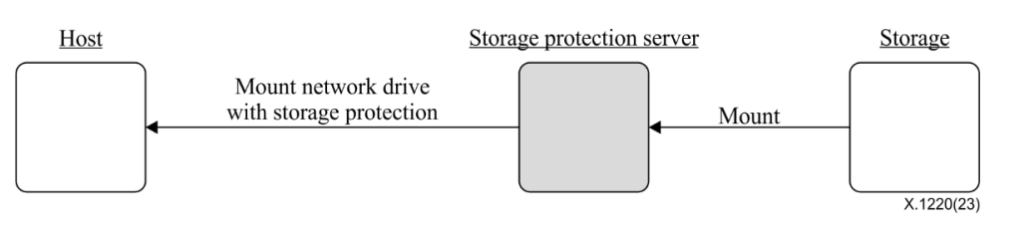
This technology is placed between endpoints and storage; whenever a program running on an endpoint requests data, it checks whether that program is pre-registered. Registered programs can read and write the real data, while unregistered programs can only access fake data.
If an unregistered program requests data, read-only fake data is provided. In other words, even if an attacker runs an exploit or malware on a PC or server to steal or encrypt files within the storage protection system, they cannot access the real data.
Most importantly, when a security officer or system operator registers an allowed program, they must input an OTP code from the PC or server so that a malicious program cannot be arbitrarily registered. Therefore, even if an endpoint is already compromised by an attacker, any program not registered via OTP cannot encrypt or delete data.
Thus, even when attacks exploiting unknown vulnerabilities or new malware attacks occur, data stored in storage protection remains safe because only allowed programs can access it.
A New Cyber Defense Paradigm Extended by Storage Protection
Given that software vulnerability and malware attacks constitute more than half of all cyber attacks, the long-standing lack of fundamental countermeasures for these attacks has been pointed out as a structural limitation of cyber security. In this context, the UN-affiliated international standardization body presenting a new alternative capable of dealing with unknown attacks represents a meaningful advance.
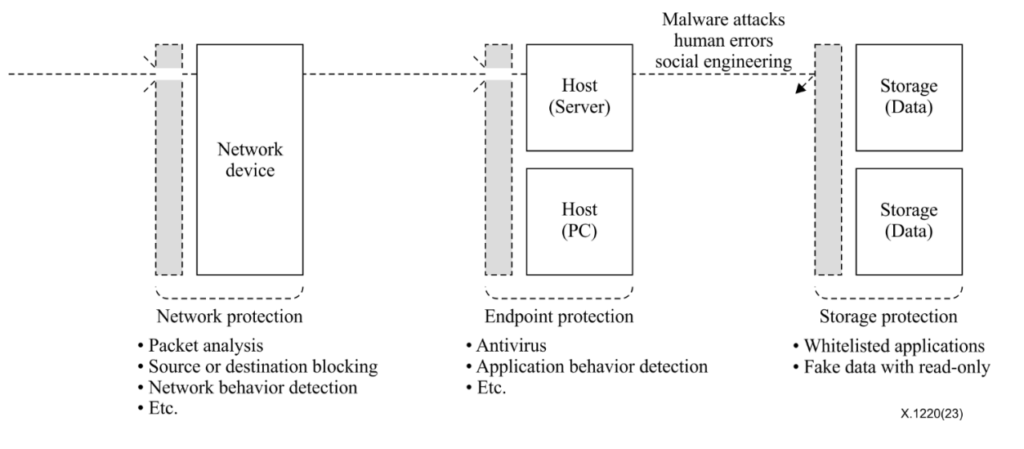
To prepare for the increasingly evolving nature of cyber attacks, a new perspective is needed that considers security at the storage layer in addition to defense-centric approaches at the network and endpoint layers. If storage is designed not as a simple data repository but as a final line of defense that attacks cannot pass through, it can complement data areas that conventional security systems have failed to address.
Going forward, we should continue to develop and expand this whitelist-based data access control model so it can be enhanced to block both vulnerability attacks and malware attacks at the storage level — effectively creating a new “security genre.” This will be more than the adoption of a single technology; it will be the first step toward fundamentally transforming the paradigm of cyber security.

